How Hackers Use Your Own Website To Extort You and Steal Information
While Google and other search engines do their best to keep the internet useful and safe, there are still loop holes designed to steal your information. Whether it’s personal photos, financial information or using your computer as a means to an end, hackers have grown more and more sophisticated over time.
One of the newest ways of attacking your data and stealing from you is through a form of extortion. It’s a malware that attacks multiple different levels of vulnerabilities called, “Ransomware.” Basically, hackers take over your website until you’ve paid them a sum of money to release it.
Clever and simple – The worst part about it is that all of it can be avoided through very simple security measures that most of us overlook. It relies on a string of failures across several different websites.
When it infects your website, it encrypts all OF your data and sends you a message asking for money, in exchange to decrypt your system. One of the more high-profile examples is the case of Presbyterian Medical Center in Hollywood, whose case was covered on wordfence.coms blog.
“In the case of Presbyterian, they had to pay 40 bitcoins or the equivalent of $17,000 to regain access to their systems. The ransomware attack affected CT scans, documentation, lab work, pharmacy functions and their email went down. Last week they paid the attacker the $17,000 and their systems were decrypted and they’re back online.” (www.wordfence.com)
This is how it works:
1. The WordPress website is hacked through either a vulnerability or forced entry. It can also be through simple means such as guessing your password.
2. Code is installed on the website. This code redirects visitors to an infected website that is running Nuclear Exploit Kit. It prevents Google from warning you as the redirects go through multiple different websites and the sites that are part of the redirect are changed.
3. Once the visitor is on the redirected site the nuclear exploit kit finds vulnerabilities in Adobe Reader, Internet Explorer, Microsoft Silverlight or a Flash Plugin.
4. Once the vulnerability is found, it installs the TeslaCrypt Ransomware.
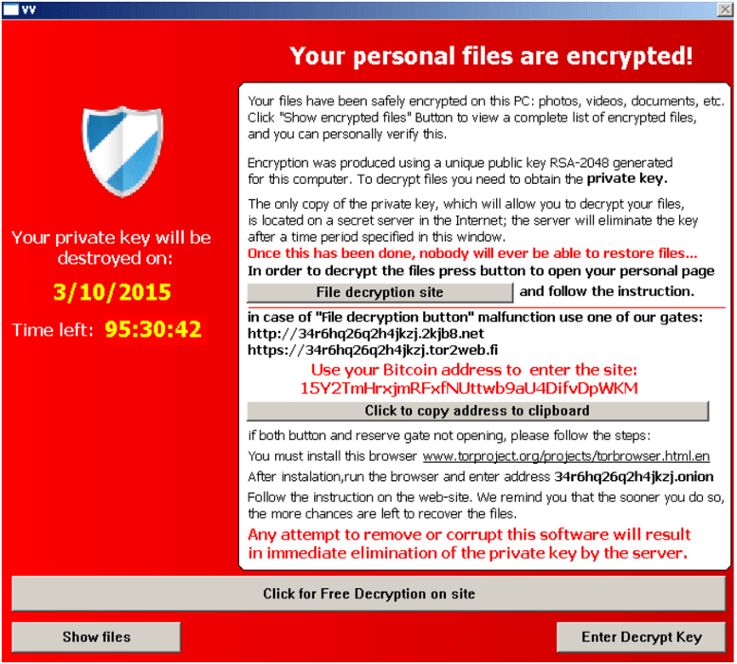
5. All files are encrytped until the owner pays a ransom to get it decrypted. Per wordfence.com, here is a picture of the warning screen.
This all sounds very confusing for the average website owner. To put it more simply, TeslaCrypt relies on loose security measures from laid back website owners or webmasters.
TAKE THE TIME TO SECURE YOUR WEBSITE!
This means they are overlooking simple yet effective website security measures such as stronger passwords or failure to update a plugin. TeslaCrypt relies on several different vulnerable WordPress websites for them to set up their redirects. It’s always scanning until it finds a string of vulnerable websites for it to use in it’s extortion scheme.
If you DO get infected by ransomware, there is a way now to get rid of it without having to pay the ransom. The way out is through TeslaCrack.
While there is a way to uncrack it, it isn’t foolproof and it’s best to just take preventive measures instead. You can easily avoid getting infected by proactive, precautionary measures.
What is a malware site by definition? According to Google’s transperancy report, “Malware sites contain code to install malicious software onto users’ computers. Hackers can use this software to capture and transmit user’ private or sensitive information”
There are also Phishing sites that “pretend to be legitimate while trying to trick users into typing in their usernames and password or sharing other private information. Common examples are web pages that impersonate legitimate bank websites or online stores”
As of October 2015, there were just under 500,000 Malware sites. The chances of you accidentally visiting one has gone up exponentially when you take these numbers into consideration. Google does its best to inform and warn visitors, but plenty of them can slip through the cracks. The TeslaCrypt is an example of this by re-routing to several other websites before Google can warn you.
There are also just under 300,000 Phishing sites impersonating reputable companies such as your bank. This has more than doubled since July of 2015.
The bottom line is that if you don’t protect your website, you are at an incredible risk of getting attacked.
How do you protect your website, your identity and your data from would be attackers?
1. Passwords: Passwords are the easiest ways hackers can exploit your system. Why are they so easy? Because people make their passwords easy. They use the same passwords for every website they login to. They are so easy most hackers can guess their way into a website setting up for an attack on your personal information.
2. Out of date WordPress plugins: Plugins need to be updated regularly for good reason.
3. Out of Date Adobe Reader, Internet Explorer, Microsoft Silverlight or a Flash Plugin. These also need to be reguarlay checked or updated.
4. 2-Step Verification: Having two-step verification on your personal g-mail or other logins can eliminate the risk completely. Google authenticator is a 2-step verification system that uses your text messaging to verify it’s you. You can install this on all of your websites to prevent TeslaCrypt from taking over.
Most people think they aren’t important enough for people to hack or steal their data. TeslaCrypt shows that they can simply use your website as a means to take over someones computer that has more ransom money.
If you are unsure how safe your website or data is, click the button below. One of our digital marketing experts will analyze your site and let you know what you can do to “beef up” security and prevent TeslaCrypt from taking over.

0 Comments